Follow these simple steps (the digital equivalent of locking your front door and not leaving your keys in the car) and you can avoid 85% of the most common digital threats out there.
Author: Cosma Papouis
Lastpass Security
I have been a very busy person over the last few months, so I have not really had time to post. But I do feel that the following warrants some time.
I have repeatedly recommended Lastpass to my friends, family and customers as a great way of storing your passwords. Unfortunately, as was bound to happen, they have suffered a security breach.
Fortunately their internal architecture was well designed (unlike some others (Sony! I’m looking at you)) and so the impact is minimal.
The Lastpass Blog gives full report from Lastpass themselves.
In Essence…
- There is nothing to worry about
- Change your Lastpass password
- Change the password of any sites that you have used the same password (bad idea anyway)
Don’t have nightmares 🙂
Contact Us to book an appointment or to discuss your needs further.
10 Sneaky things a spammer will do
The attached ebook talks about 10 Sneaky things a spammer will do to get past your spam filters.
10 sneaky things a spammer will do
The last 2 pages are an advert for Dell Sonicwall firewalls, but you can skip them, the rest of the information is interesting.
Contact Us to book an appointment or to discuss your needs further.
Internet Backup
I am a member of a business networking group that also has a group on linked in. Recently a member asked…
Can you tell me anything about Livedrive? My backup man says he wouldn’t trust it with his data and my computer man swears by it. I am currently on it, but would prefer to have my data a bit nearer to me.
I started to answer the question and quickly realised that the answer may be of broader interest, and so here it is… (I seem to have wittered on for a while longer than intended. You may wish to skip to the summary)
I can’t tell you about LiveDrive specifically, as I have never used them. However having looked at their website I can tell you that they say all the right things. Unlimited, Data stored in UK, apps so you can get to your data from anywhere. They imply that they do versioning of files, but it is not clear if you can access the versions directly or if you have to ask LiveDrive to provide previous versions.
Your IT man is correct and your backup man needs to move in to the 21st century. Tell him to go to the library and get a book about this strange thing called the “Internet”. I hate to be rude, but it amazing how many IT folk are burying their heads in the sand and hoping the internet will go away, instead of embracing it and the opportunities it provides.
There are many backup strategies that you can use. The current favoured approach is called 321. No file is thought of as existing until you have…. 3 Copies on… 2 Different Media… 1 of them off site To this end an off-site backup provider serves as 2 different media (your hard disk and their storage system) and obviously it is Off-Site. To satisfy the 3 copies rule I do a number of thing…
- I use Carbonite (Similar to Livedrive)
- I have a local hard disk that I back up to (but like all normal people, this is sporadic – in fact I think I will make a backup now!)
- My documents folder is replicated to Microsoft One Drive and to Cubby (this has the benefit of ensuring that a, my business partner and I always have the same files to work on and b, there is always a copy on my business partners laptop as well as mine (and yes, he uses Carbonite as well)).
Please see this short blog entry about how this setup saved my bacon!
What are your concerns and why do you want to have your data near you?
I will try and address major concerns below and hopefully cover yours.
- Is the data secure? That depends on what you mean by secure. If you mean “Safe from Loss”, then yes. Typically the backup provider will have data centres in secure locations and will duplicate your data on more than 1 location. If you mean “Can the backup provider see my files” the answer is “it depends”. With the provider I use (Carbonite) the data is encrypted from me to them. I believe it is encrypted on their servers. I have chosen to let them manage the keys, which allows me to use the apps to access my data from anywhere. I do have the option to manage the keys myself. This means that they CANNOT see any of my data, but also means that a, I cannot use the apps they provide and b, I have to manage the keys (if I lose them I am in deep trouble).
- How quickly can I get to my data? Well. That is dependent on your internet connection and how much data you have. Some backup providers will ship you a DVD or disk with your data on (for a fee). This is where a local backup helps.
Summary
In short Internet Backup Good!
Contact Us to book an appointment or to discuss your needs further.
5 passwords you should never use
|
|
|
|
|
Microsoft respects your privacy. If you would prefer not to receive The Microsoft Security for Home Users To set your contact preferences for other Microsoft communications click here. Microsoft Corporation One Microsoft Way Redmond, WA 98052 USA |
I just got this error message – true or scam? If so, what do I do?
It seems that all we are posting about recently is scams and issues. Unfortunately the bad guys are active and this information needs repeating, until people stop clicking on random links….
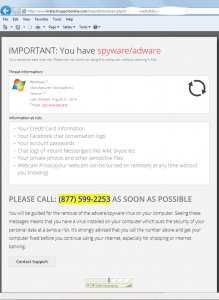
The following error was seen by one of our clients this week. He received a warning email and, counter to all advice given, clicked on the link, which took him to this page….
His question was “true or scam? If so, what do I do?”
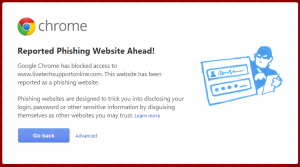
It’s a scam! We clicked on the link (in a sandboxed, safe, environment) using Google Chrome and received a message telling us it is a phishing site (see below). It’s a shame he was using an older version of Internet Explorer that does not show these warnings.
 The irony is that most the information on the 1st web page is actually correct! Except it is describing the situation you will be in if you follow the instructions. If you call the number (note that it is a US number and my user is in the UK) you will speak to a person that will guide you through a “diagnostic process”, you will then be guided to a web site to download some “clean up”tools. This is where the trouble begins (this is all well documented and so there is no purpose to me repeating the info here. Just Google “Tech Support Scam”).
The irony is that most the information on the 1st web page is actually correct! Except it is describing the situation you will be in if you follow the instructions. If you call the number (note that it is a US number and my user is in the UK) you will speak to a person that will guide you through a “diagnostic process”, you will then be guided to a web site to download some “clean up”tools. This is where the trouble begins (this is all well documented and so there is no purpose to me repeating the info here. Just Google “Tech Support Scam”).
If so, what do I do?
Well, step -1 is DO NOT CLICK ON LINKS IN UNSOLICITED EMAILS! Failing that, step 1 is, delete the original email message. Step 2 is, close the web page and it is probably a good idea to clear your web cache.
Step 3, assuming that you have not executed any programs, or gone to any more web pages as directed by the scammer, don’t worry about it – you are probably ok.
You can at this stage run some malware scanners (Malwarebytes, Spybot, et al…), just to make yourself feel better.
Internet Explorer has improved massively in recent versions and, some would argue, is as secure as the other major browsers. We remain to be convinced, and would definitely not recommend using any versions of IE before V11. We would always suggest that you use either Chrome or Firefox (updated to the latest versions).
Contact Us to book an appointment or to discuss your needs further.
New variation on an old scam
This seems to be becoming a bit of a recurring theme, there’s a new scam out there.
This one is actually not a new scam, it’s an old scam that simply uses a new script.
The proposed victim gets a phone call saying that they (the scammers) are from Microsoft and that…
- There are 5 other people using the victims Windows licence key.
- That it is unsafe for the victim to use internet services; for example Mobile Banking.
- That the victims Windows licence key could be cancelled by Microsoft.
How’s that for a scare tactic?
The scammers then want the victim to go to www.ammyy.com and download the remote admin software they have there.
Ammyy have a warning on their site saying that their software is being used by people purporting to be from Microsoft to ‘fix’ the computer using Ammyy Amin, it’s definitely a scam.
At least they are aware of the problem.
We at UATS have seen occurrences of (or variations of) this scam and have experienced it ourselves. Ultimately the scammers just want you to download and run a ‘fix’, which is where the real pain begins.
Word has spread about the earlier version of this scam and so they have changed the script (but are still using basically the same underlying technology) to try to ensnare the average user.
As always I will refer you to our Keeping Safe on the Internet page and leave you with the thought… If you are not sure then just do not click on it! Go and ask someone who is sure.
Contact Us to book an appointment or to discuss your needs further.
Avoid tech support phone scams
It appears that an old spectre has reared its ugly head again.
Fake tech support phone scams
We had thought that they had slowed down as we have not had one reported to us for quite some time, but it appears that the scammers are still going strong. We will not go into chapter and verse here with advice and information, so much has already been written.
http://www.microsoft.com/en-gb/security/online-privacy/avoid-phone-scams.aspx
http://www.microsoft.com/en-gb/security/online-privacy/msname.aspx
These links are from Microsoft, but it apply equally well to other callers. In fact the call that was received today identified itself as being from BT
The same advice as always applies – Keeping Safe on the Internet
In essence, don’t click on it unless you are 100% sure it is legitimate, never click on it if it was unsolicited etc… (The callers try to get you to go to a website where they have you download and run some software that will “protect” you or will “scan” your machine. What they are really doing is using you to infect your own machine).
The links above are legitimate Microsoft sites, but please don’t take our word for it. Try Googling “Microsoft avoid phone scams” or “Avoid scams that use the Microsoft name fraudulently“
Treat calls like this as you would if you bumped into a person on the street with a Microsoft or BT hat on. Would you give a total stranger your credit card information? No? Of course not. So don’t do it on the internet unless you went looking for the service and you are as confident as possible that the provider is who they say they are.
Contact Us to book an appointment or to discuss your needs further.
Yes, Virginia, TrueCrypt is still safe to use
TrueCrypt, a fantastic free whole disk encryption tool has recently vanished of the face of the planet. No one quite knows why, but everyone is wondering if it is safe to use (the last comments from the authors tend to indicate that it is not!).
Rather than reinventing the wheel, I thought I would pass on the following blog entry by Steve Gibson, a respected Tech/Security Guru, that gives his take on it and an answer to the question “Is TrueCrypt safe to use?”
Steve Gibson posted: “So opens the short editorial I wrote this morning and placed at the top of GRC’s new TrueCrypt Final Version Repository page. The impetus for the editorial was the continual influx of questions from people asking whether TrueCrypt was still safe to”
|
Contact Us to book an appointment or to discuss your needs further.
Social Engineering?
Why Phishing Scams Keep Working
Think before you click
The internet is riddled with scams and virus’ that continue to persists well past their “Sell By” date. There are many reasons for this; unpatched software, unpatched Operating Systems (OS’s) (would you belive that there are still Windows 95 machines out there, that have not been updated in years, that are compromised, but carry on working, doing what ever task they were set up for in the first place and being a nuisance for the rest of us).
We often hear about people being “hacked”; as with the “phone hacking” that caused the end of the News of the World, but the reality is that many (most) of these so called hacks are actually Social Engineering attacks; someone is duped to hand over information that helps the “hacker” (either verbally or in this case via a web page) or people’s normal behaviour is leveraged (in the case of the phone hacking they took advantage of the fact that most people do not change their voicemail’s default password).
Windows XP has now gone out of support, but this need not be a problem if you use a secure browser (Firefox. Chrome, et al (but not IE)) you keep an upto date virus scanner and …
Think before you click











 < ![endif]>
< ![endif]>